Deploying certificates from different Certificate Templates via NDES and Intune
My name is Saurabh Sarkar and I am an Intune engineer in Microsoft. I have a YouTube channel ‘EverythingAboutIntune’ and you can subscribe to the same to learn more about Microsoft Intune.
Use Case:
- There are many scenarios wherein the customers want to deploy different certificates via NDES (each of them having conflicting settings)
- This is typically the case when both the certificates need different hash algorithm/keysize bits etc..
- In such situation we cannot utilize the same certificate template to deploy both kinds of certificates as the settings in each is contradict each other.
- In this article we will understand how we can leverage the same Issuing CA and NDES to deploy certificates originating from different certificate template.
Concept
There are 3 things that work behind the scenes which together determines which certificate template would be used to issue the certificate to the end device.
1- The Key Usage selected in the SCEP profile in Intune
2- The Name of the template in the relevant registry of the NDES server
3- The ‘Purpose’ of the certificate template as viewed in the CA
The values in all the above 3 locations need to be corresponding for a successful certificate delivery. If we make this configuration correctly, then we can achieve the use case of deploying certificates from different templates via the same NDES using Intune.
| Key Usage (in SCEP Profile) | Corresponding Registry | Purpose (as per the Certificate Template) |
| Digital Signature | SignatureTemplate | Signature |
| Key encipherment | EncryptionTemplate | Encryption |
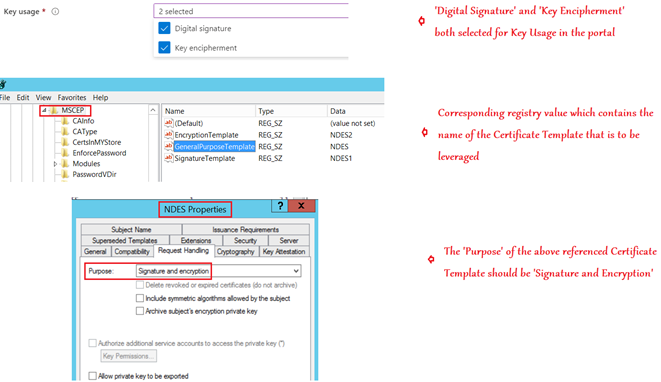
| Digital signature and Key encipherment | GeneralPurposeTemplate | Signature and Encryption |
Understanding the Relevant Flow:
- The SCEP Profile is created by the admin in the portal.
- The profile payload is received by the device.
- The device sends the csr (which contains the information from the payload) to the NDES.
- NDES does the needed validation of the csr
- Depending upon the “Key Usage” in the SCEP payload the corresponding registry location is referenced.
- The CRP utilizes the configured NDES service account and sends the request to the CA requesting for a certificate on behalf of the user.
- The CA will check-
- If the Template name is correct or not
- If the referenced template is published in the CA or not
- If the account requesting for the certificate has ‘Enroll’ permissions or not
- If the attributes in the csr(like the certificate validity etc.. as set in the profile) is in accordance with the validity of the certificate template or not.
Amongst other things, the important check made at this point is-
Making sure that the “Purpose” of the Certificate Template from which the certificate is being requested is in accordance with the Key Usage from the profile (i.e. the csr)
Example Use case:
#Requirement-
Pushing certificates from 3 different Certificate Templates via the same NDES and CA infrastructure.
#Setting done at the CA:
- We need to publish 3 different certificate templates at the CA.
- Each of these templates will have a different ‘Purpose’ and will be referenced accordingly.
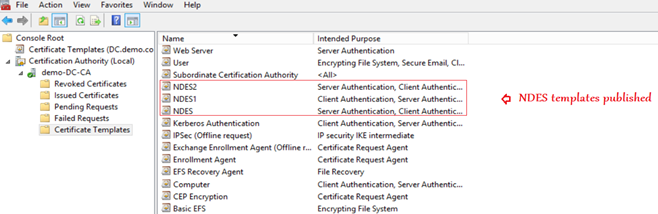
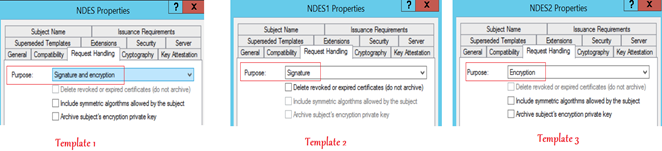
Scenario 1:
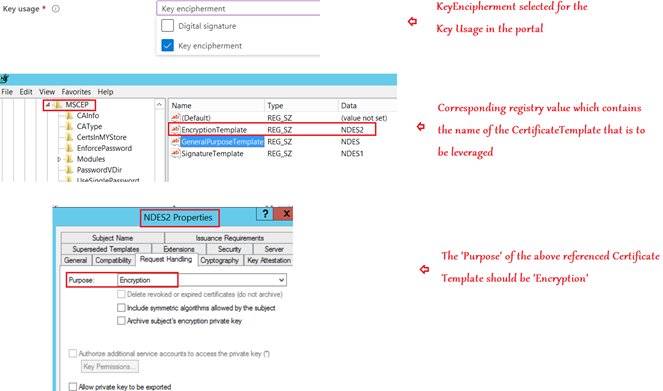
- If the Key Usage selected in the SCEP profile is “Digital Signature” then the template name from the “SignatureTemplate” registry will be fetched and that template must have a purpose of ‘Signature’.
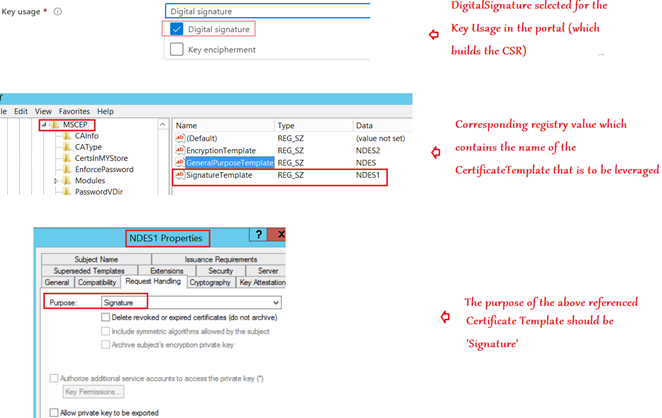
Scenario 2:
- Similarly, if the Key Usage selected in the SCEP profile is “Key Encipherment” then the template name from the “EncryptionTemplate” registry will be fetched and that template must have a purpose of ‘Encryption’.
Scenario 3:
- Similarly, if the Key usage in the SCEP profile was both “Digital Signature and Key Encipherment” then the template name from the “GeneralPurposeTemplate” registry will be fetched and that template must have a purpose of ‘Signature and Encryption’.
Conclusion:
So this means, that as per our requirement we can possibly issue certificates originating from 3 different Certificate Templates at a time via NDES and Intune (without making any changes to the active setup)
- As we can see below, there are certificates issued from 3 different templates (viz, NDES, NDES1 and NDES2)
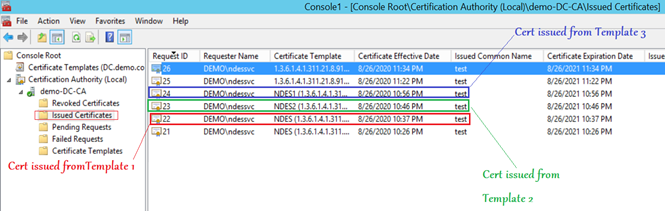
- The above was achieved by pushing 3 different SCEP profiles via Intune (having Key Usage as- Digital Signature, Key Encipherment, Digital Signature+Key Encipherment) respectively.
- We published 3 different Certificate Templates in the CA with relevant ‘Purpose’
- The respective registry was populated accordingly in the NDES server.
I hope this article has been helpful in understanding how we can leverage the same NDES and CA setup to push certificates originating from different certificate templates.
