Managing Chrome, Firefox in Windows with Intune using OMA-URIs(1/3)

In this article, we are going to discuss how to manage Chrome and Firefox in Windows from Intune by deploying OMA-URIs.!
My name Saurabh Sarkar and I am an Intune engineer in Microsoft. I have a YouTube channel and you can subscribe to the same to learn more about Microsoft Intune.
Background:
We very often get requirement from customers wherein they wish to protect the data in the browser of their Windows 10 machines given that the same is used for accessing many enterprise application\resources.
Now from Intune we have the ability of managing IE and Edge for Windows via making use of the Windows Information Protection Policy (WIP). However conventionally the same cannot be leveraged out of the box for Chrome and Mozilla Firefox given that they are not enlightened applications (i.e. they are not MAM aware apps and cannot differentiate between corporate\personal data and comprehend the WIP policy)
Please refer to my below article which explains the difference b/w Enlightened and Un-enlightened application- https://techcommunity.microsoft.com/t5/intune-customer-success/support-tip-taking-a-look-at-wip-and-enlightened-vs/ba-p/499715
In this article I wanted to take a moment and discuss the various methods of managing Google Chrome and Mozilla Firefox via Intune in a Windows 10 device with emphasis on OMA-URIs
Sidenote
#Even though we are transitioning to the new Chromium based Edge, we still have customers making use of Google Chrome\Firefox browser and wish to protect the corporate data within.
#As illustrated herein, the usage of OMA-URI is a workaround (if the customer chooses to protect the data in 3rd party browser) and it does not make the browser enlightened.
#This is not a recommendation to customers from support perspective, it’s an elucidative
Overview:
As mentioned, given that Google Chrome and Firefox are not enlightened apps, they cannot be targeted via WIP policy. However, there are the below 3 possible ways of administering Chrome from Intune thereby protecting the enterprise data in the browser.
| S.No. | Approach | Applicability |
| 1 | Managing Chrome Browser via OMA-URIs using ‘Chrome – ADMX’ | Applicable for Chrome only |
| 2 | Making use of Windows Defender Application Guard (WDAG) | Applicable for Chrome, Firefox, IE and Edge |
| 3 | Using an Applocker xml for the browser | Applicable for Chrome and Firefox |
In this article, I wanted to take a moment and discuss the first options. The other 2 options has been explained in a different post
Managing Chrome browser from Intune via OMA-URIs using ‘Chrome – ADMX’
*Sidenote- This can also be done via GPO which is explained in the below doc-https://docs.microsoft.com/en-us/archive/blogs/ukplatforms/google-chrome-gpo-via-intune
We can manage Google Chrome from Intune by pushing a Device configuration profile in which we will define the attributes of Chrome we wish to manage.
In this article we will push a policy and blacklist a couple of URLs viz youtube.com and cricbuzz.com (this is one of the possible use cases)
This would ensure that Chrome is being used for accessing all the websites except for accessing the URLs that have been blacklisted for which the user would have to go to edge wherein the data would remain protected via WIP policy.
How to achieve the above:
To achieve the above, we must push 2 device configuration profiles from Intune.
- The first profile is used for pushing the Chrome-admx.( Ingesting the ADMX) which is explained below
- The second profile is used for referencing/calling a function from the first profile (the above ADMX)
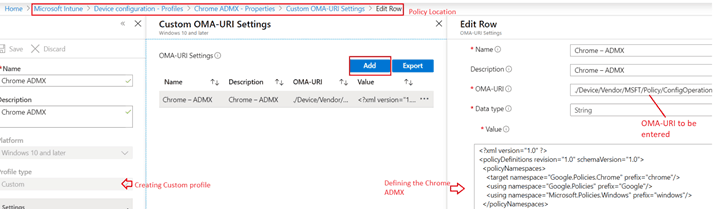
1-Ingesting the Chrome ADMX
In this device configuration profile we are pushing the chrome admx which in a way is defining all the functions that can be possibly used in managing chrome browser(like blacklisting urls\while listing urls\setting homepage\allowing-blocking cookies etc)
- #Go to Microsoft Intune>Device Configuration>Windows 10>Custom Type>Click on Add.
- #OMA-URI to be entered here- ./Device/Vendor/MSFT/Policy/ConfigOperations/ADMXInstall/Chrome/Policy/ChromeAdmx
- #In the value field we will define the Chrome ADMX. The value to be entered here is present in the link-https://support.google.com/chrome/a/answer/9102677?hl=en
Now assign this to a user group who has enrolled the device.
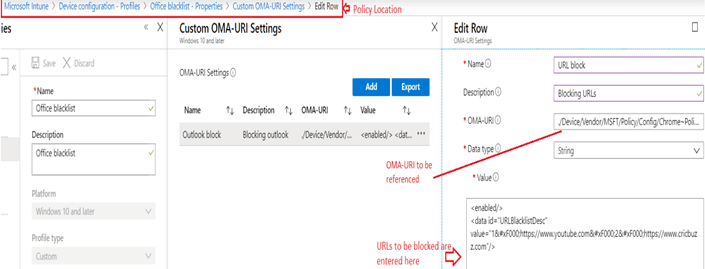
2-Referencing the ADMX
The second profile is used to call\reference one of the functions in the first profile- in our case “/URLBlacklist“
How to do the same:
- #Go to Microsoft Intune>Device Configuration>Windows 10>Custom Type>Click on Add.
- #Now we will have to select options as displayed below-
- #OMA-URI to be entered here- ./Device/Vendor/MSFT/Policy/Config/Chrome~Policy~googlechrome/URLBlacklist
- #In this we are referencing the “URLBlacklist” function defined in the 1st profile.
- For testing, I defined https://youtube.com and htts://www.cricbuzz.com in the profile which I wished to blacklist.
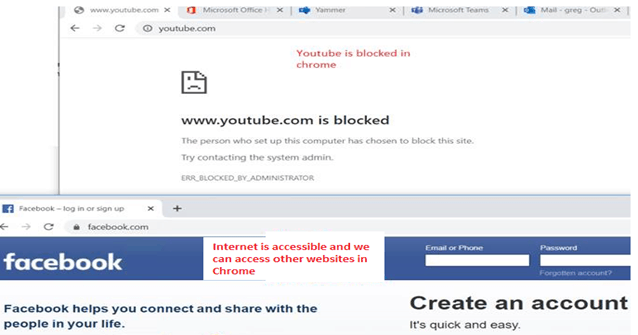
Results of Block URLS – Observed Behavior:
Both the websites targeted in the above profile were blocked but all the other URLs were accessible in the Chrome browser as shown below:
How to Validate Chrome Block URL settings?
Once the policy has been deployed, there are 3 locations wherein we can validate the same at the device end viz-
- #- Registry
- #- Chrome browser
- #-MDM (Info>Sync)
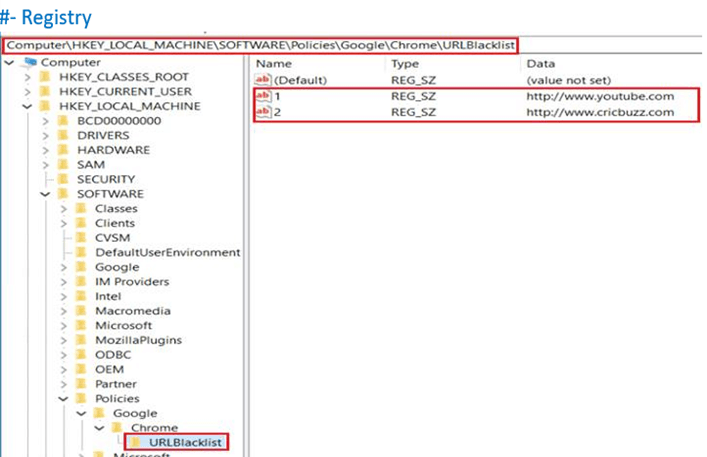
–>As illustrated, in the above registry location we can see the URLs that are being blacklisted by the policy.
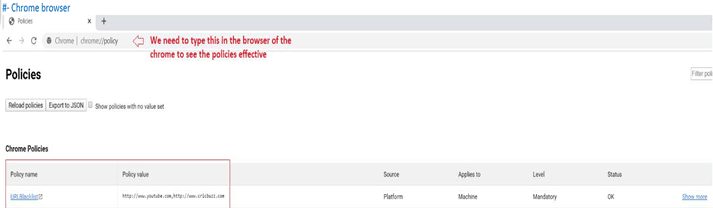
–>This way we can see the policy coming down to the browser and the urls that are being blocked.
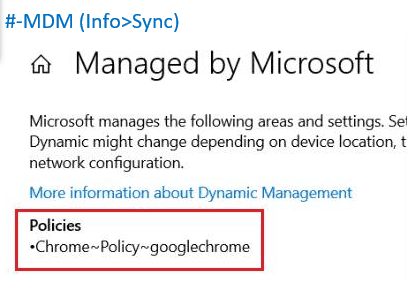
Net Result:
- As an admin we now have the option of whitelisting\blacklisting URLs thereby determining which websites would be accessible\would not be accessible from the browser.
- We can configure the wallpaper image that is shown on the desktop
- We can control the availability of fullscreen mode in which all Google Chrome UI is hidden and only web content is visible
- We can ImportBookmarks, ImportHistory, ImportHomepage, IncognitoModeAvailability
- We can set the languages that can be used as the preferred language.
- Above are some of the possible usecases. The level of administration of Google Chrome via this approach is very granular as listed in the above link.
- We cannot administer the behavior of data movement from Chrome to any other application using this approach or prevent leakage of data
Conclusion:
There are multiple ways of managing Chrome and Firefox in a Windows 10 machine from Intune as illustrated above.
We can use either of them or a combination of them depending upon the use case and the level of restriction we wish to impose on the user’s browser session.
Other relevant URLs:
- https://cloud.google.com/docs/chrome-enterprise/policies/?policy=URLBlacklist https://www.chromium.org/administrators/url-blacklist-filter-format
- https://support.google.com/chrome/a/answer/7532419?hl=en
- Intune Application Deployment Guide Google Chrome Browser
