Managing Chrome and Firefox in Windows from Intune using Applocker(3/3)

In this article, we are going to discuss how to Use Applocker to Manage Chrome & Firefox in Windows from Intune.

My name Saurabh Sarkar and I am an Intune engineer in Microsoft. I have a YouTube channel and you can subscribe to the same to learn more about Microsoft Intune.
Background:
We very often get requirement from customers wherein they wish to protect the data in the browser of their Windows 10 machines given that the same is used for accessing many enterprise application\resources.
Now from Intune we have the ability of managing IE and Edge for Windows via making use of the Windows Information Protection Policy (WIP). However conventionally the same cannot be leveraged out of the box for Chrome and Mozilla Firefox given that they are not enlightened applications (i.e. they are not MAM aware apps and cannot differentiate between corporate\personal data and comprehend the WIP policy)
Please refer to my below article which explains the difference b/w Enlightened and Un-enlightened application- https://techcommunity.microsoft.com/t5/intune-customer-success/support-tip-taking-a-look-at-wip-and-enlightened-vs/ba-p/499715
In this article, I wanted to take a moment and discuss the various methods of managing Google Chrome and Mozilla Firefox via Intune in a Windows 10 device with an emphasis on the Applocker file.
Sidenote
- Even though we are transitioning to the new Chromium-based Edge, we still have customers making use of the Google Chrome\Firefox browser and wish to protect the corporate data within.
- As illustrated in the kb, the usage of OMA-URI\WDAG\Applocker XML is a workaround (if the customer chooses to protect the data in 3rd party browser) and it does not make the browser enlightened.
- #This is not a recommendation to customers from a support perspective, it’s elucidative.
Overview:
As mentioned in Part 1, there are the below 3 possible ways of administering Chrome from Intune thereby protecting the enterprise data in the browser.
| S.No. | Approach | Applicability |
| 1 | Managing Chrome Browser via OMA-URIs using ‘Chrome – ADMX’ | Applicable for Chrome only |
| 2 | Making use of Windows Defender Application Guard (WDAG) | Applicable for Chrome, Firefox, IE and Edge |
| 3 | Using an Applocker xml for the browser | Applicable for Chrome and Firefox |
In this article, I wanted to take a moment and discuss the third option. The first 2 have been explained in previous posts.
Using an Applocker XML for Chrome & Firefox
We would traditionally use this approach if we want to make Chrome\Firefox as a managed application from Intune(i.e. if we want it to behave almost the same way any enlightened application behaves- can be used to restrict leakage of data to an unmanaged application.
Since Google Chrome is NOT an enlightened application by default, we can make use of an Applocker file to achieve a similar purpose which makes google chrome a managed application.
(Note- The application becomes “Managed” and not “Enlightened” via the use of app locker file)
- More clarification on the same at- https://techcommunity.microsoft.com/t5/Intune-Customer-Success/Support-Tip-Taking-a-look-at-WIP-and-Enlightened-vs/ba-p/499715
- More details: https://techcommunity.microsoft.com/t5/core-infrastructure-and-security/applocker-8211-another-layer-in-the-defense-in-depth-against/ba-p/258768
How to Build Applocker Chrome Firefox
We will have to create an Applocker file and then deploy it to a user via WIP policy. The file can be generated form any Windows 10 machine wherein Google Chrome\Firefox has been installed.
How to create applocker: https://techcommunity.microsoft.com/t5/intune-customer-success/support-tip-using-applocker-to-create-custom-intune-policies-for/ba-p/364981
An applocker for chrome would look like below-
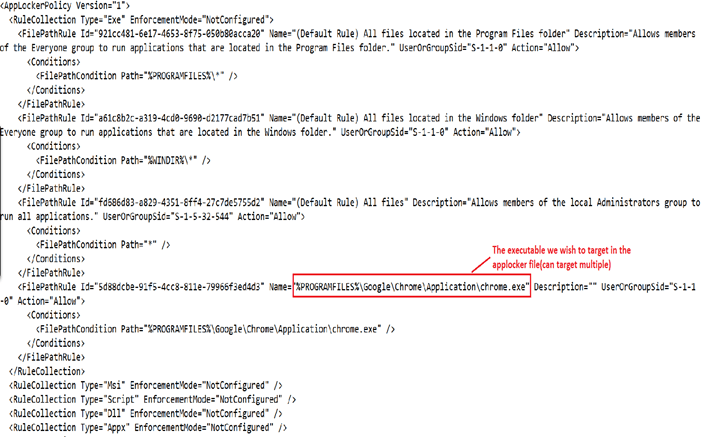
The above file needs to be uploaded in .xml format in the WIP policy in the below location.
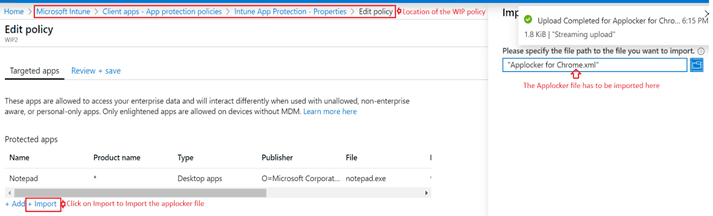
Rest of the settings in the WIP policy would be as applicable.
Outcome:
Now the data leakage from Chrome\Firefox to any unmanaged application is going to be protected.
However If the user opens 2 tabs in chrome- first Gmail(personal) and second owa (corporate)- he would be able to move data between the two as the data is staying within the managed application.
This approach is basically used for protecting and limiting data within an un-enlightened application which has now been made managed (which otherwise without the usage of applocker cannot be done)
Verification – Observation
- After the Applocker is pushed via the WIP policy.
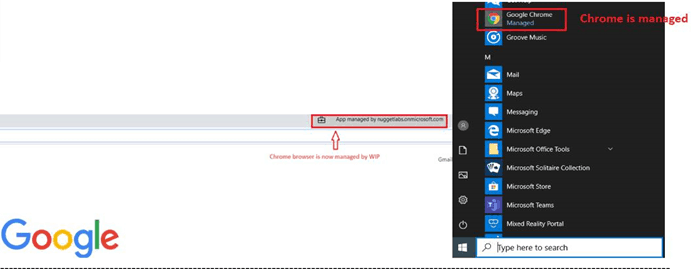
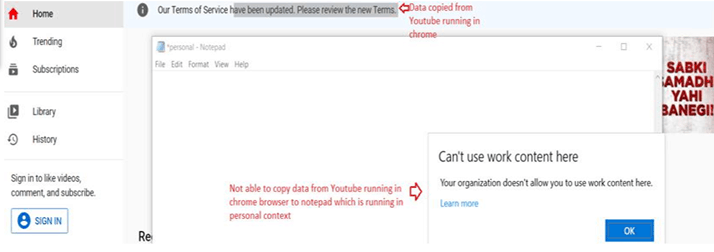
The experience is similar for both Firefox and Chrome once the relevant Applocker file is in place.
Net Result:
Using this approach, we can:
- Make Chrome\FireFox a managed application.
- Now Chrome\FireFox can receive data\send data from\to any other managed application in the device.
- The cut\copy\paste behavior in the browser is not supervised and we can administer the lekage of data from this browser to any unmanaged application.
- The functionality using this approach alone is limited as we cannot segregate the experience based on the type of URL being accessed from the browser.
- Using Aplocker for multiple applications sometimes malfunctions so this is not the best way of managing an application via Intune
Conclusion:
There are multiple ways of managing Chrome and Firefox in a Windows 10 machine from Intune as illustrated above.
We can use either of them or a combination of them depending upon the use case and the level of restriction we wish to impose on the user’s browser session.
Resources
- https://cloud.google.com/docs/chrome-enterprise/policies/?policy=URLBlacklist https://www.chromium.org/administrators/url-blacklist-filter-format
- https://support.google.com/chrome/a/answer/7532419?hl=en
- Intune Application Deployment Guide Google Chrome Browser

Comments
hello, your post is very good.Following your articles.